Types of wireless LANs[edit]
The IEEE 802.11 has two basic modes of operation: infrastructure and ad hoc mode. In ad hoc mode, mobile units communicate directly peer-to-peer. In infrastructure mode, mobile units communicate through a wireless access point (WAP) that also serves as a bridge to other networks such as a local area network or the Internet.
Since wireless communication uses a more open medium for communication in comparison to wired LANs, the 802.11 designers also included encryption mechanisms: Wired Equivalent Privacy (WEP), no longer considered secure, Wi-Fi Protected Access (WPA, WPA2, WPA3), to secure wireless computer networks. Many access points will also offer Wi-Fi Protected Setup, a quick, but no longer considered secure, method of joining a new device to an encrypted network.
Infrastructure[edit]
Most Wi-Fi networks are deployed in infrastructure mode. In infrastructure mode, wireless clients, such as laptops and smartphones, connect to the WAP to join the network. The WAP usually has a wired network connection and may have permanent wireless connections to other WAPs.
WAPs are usually fixed and provide service to their client nodes within range. Some networks will have multiple WAPs using the same SSID and security arrangement. In that case, connecting to any WAP on that network joins the client to the network, and the client software will try to choose the WAP that gives the best service, such as the WAP with the strongest signal.
Peer-to-peer[edit]
An ad hoc network is a network where stations communicate only peer-to-peer (P2P). There is no base and no one gives permission to talk. This is accomplished using the Independent Basic Service Set (IBSS). A Wi-Fi Direct network is a different type of wireless network where stations communicate peer-to-peer.[4] In a peer-to-peer network wireless devices within range of each other can discover and communicate directly without involving central access points.
In a Wi-Fi P2P group, the group owner operates as an access point and all other devices are clients. There are two main methods to establish a group owner in the Wi-Fi Direct group. In one approach, the user sets up a P2P group owner manually. This method is also known as autonomous group owner (autonomous GO). In the second method, called negotiation-based group creation, two devices compete based on the group owner intent value. The device with higher intent value becomes a group owner and the second device becomes a client. Group owner intent value can depend on whether the wireless device performs a cross-connection between an infrastructure WLAN service and a P2P group, available power in the wireless device, whether the wireless device is already a group owner in another group or a received signal strength of the first wireless device.
IEEE 802.11 defines the PHY and medium access control (MAC) layers based on carrier-sense multiple access with collision avoidance (CSMA/CA). This is in contrast to Ethernet which uses carrier-sense multiple access with collision detection (CSMA/CD). The 802.11 specification includes provisions designed to minimize collisions because mobile units have to contend with the hidden node problem where two mobile units may both be in range of a common access point, but out of range of each other.
Bridge[edit]
A bridge can be used to connect networks, typically of different types. A wireless Ethernet bridge allows the connection of devices on a wired Ethernet network to a wireless network. The bridge acts as the connection point to the wireless LAN.
Wireless distribution system[edit]
A wireless distribution system (WDS) enables the wireless interconnection of access points in an IEEE 802.11 network. It allows a wireless network to be expanded using multiple access points without the need for a wired backbone to link them, as is traditionally required. The notable advantage of a WDS over some other solutions is that it preserves the MAC addresses of client packets across links between access points.[5]
An access point can be either a main, relay, or remote base station. A main base station is typically connected to the wired Ethernet. A relay base station relays data between remote base stations, wireless clients or other relay stations to either a main or another relay base station. A remote base station accepts connections from wireless clients and passes them to relay or main stations.
Because data is forwarded wirelessly, consuming wireless bandwidth, throughput in this method is halved for wireless clients not connected to a main base station. Connections between base stations are done at layer-2 and do not involve or require layer-3 IP addresses. WDS capability may also be referred to as repeater mode because it appears to bridge and accept wireless clients at the same time (unlike traditional bridging). All base stations in a WDS must be configured to use the same radio channel, and share WEP keys or WPA keys if they are used. They can be configured to different service set identifiers. WDS also requires that every base station be configured to forward to others in the system as mentioned above.
Roaming[edit]
There are two definitions for wireless LAN roaming:
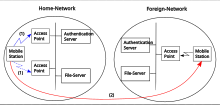
- Internal roaming: The mobile station (MS) moves from one access point (AP) to another AP within a home network if the signal strength is too weak. An authentication server performs the re-authentication of MS via 802.1x (e.g. with PEAP). The billing of QoS is in the home network. A MS roaming from one access point to another often interrupts the flow of data between the MS and an application connected to the network. The MS, for instance, periodically monitors the presence of alternative APs (ones that will provide a better connection). At some point, based on proprietary mechanisms, the MS decides to re-associate with an AP having a stronger wireless signal. The MS, however, may lose a connection with an AP before associating with another access point. To provide reliable connections with applications, the MS must generally include software that provides session persistence.[6]
- External roaming: The MS (client) moves into a WLAN of another wireless Internet service provider (WISP) and takes their services. The user can use a foreign network independently from their home network, provided that the foreign network allows visiting users on their network. There must be special authentication and billing systems for mobile services in a foreign network.[clarification needed][citation needed]
See also[edit]
You received this message because you are subscribed to the Google Groups "1TopReadys1" group.
To unsubscribe from this group and stop receiving emails from it, send an email to 1topreadys1+unsubscribe@googlegroups.com.
To view this discussion on the web visit https://groups.google.com/d/msgid/1topreadys1/CAForgrR1G%3Dvo%2BM-OeA_yR-BEv7LJ1wPTAM7oTUw4PoUT-%3DaoXg%40mail.gmail.com.
No comments:
Post a Comment